|
|||||||
|
|||||||||||
| Biometrics Direct - Your Source for Fingerprint Biometric Security Products for Home, Travel and Office |
|
|
|
|
|
|
||||||||||||||||
|
Glossary of Common Biometric and Security Related Terms -
Some definitions provided by Wikipedia
Advanced Encryption Standard (AES), also known as Rijndael, is a block cipher adopted as an encryption standard by the US government. It is expected to be used worldwide and analyzed extensively, as was the case with its predecessor, the Data Encryption Standard (DES). AES was adopted by National Institute of Standards and Technology (NIST) as US FIPS PUB 197 in November 2001 after a 5-year standardization process. The cipher was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, and submitted to the AES selection process under the name "Rijndael", a portmanteau comprising the names of the inventors. Rijndael is pronounced a bit like "Rhine dahl", with a long "i" and a silent "e". (Wikipedia.org)
Algorithm A limited set of well-defined instructions to solve a task, which leads reliably from a given starting point to a corresponding identifiable end point. It can also be described as a systematic procedure for carrying out a calculation or solving a problem in a limited number of stages. Many algorithms can be implemented as computer programs. In biometric systems, specific algorithms are used, for example, to indicate how a smart card determines whether the input fingerprint matches the template stored on the card or in the database. ANSI 378 Refers to interoperability standard for fingerprint templates developed by the American National Standards Institute (ANSI). The US governmental requires the use of ANSI 378 templates for Homeland Security Directive (HSPD-12) and Personal Identity Verification (PIV). The US Federal requirements for ANSI 378 are designed to ensure that all employees and contractors are able to use their badges for identification and access to all government facilities. Automated Fingerprint Identification System (or AFIS) is a system to automatically match one or many unknown fingerprints against a database of known prints. This is done for miscellaneous reasons, not the least of which is because the person has committed a crime. With greater frequency in recent years, AFIS like systems have been used in civil identification projects. The intended purpose is to prevent multiple enrollment in an election, welfare, DMV or similar system. The FBI manages a fingerprint identification system and database called IAFIS, which currently holds the fingerprints and criminal records of over fifty-one million criminal record subjects, and over 1.5 million civil (non-criminal) fingerprint records. US Visit currently holds a repository of over 50 million persons, primarily in the form of two-finger records (by 2008, US Visit is transforming to a system recording FBI-standard tenprint records). (Wikipedia.org) Authentication Any systematic method of confirming the identity of an individual. Some methods are more secure than others. Simple authentication methods include user name and password, while more secure methods include token-based one-time passwords. The most secure authentication methods include layered or "multi-factor biometric procedures. This is independent of authorization. 1-factor authentication The classic fingerprint-without-card technology is simple and in many cases what serves our customersí basic needs best. The fingerprint reader solution replaces codes or passwords.
Authorization The administration of person-specific rights, privileges, or access to data or corporate resources. Biometrics The automatic recognition of persons based on unique combinations of measurable physical or behavioral characteristics. Examples include fingerprints, iris scanning, face and voice recognition, or hand geometry. All of these biometric techniques are differentiated by speed, durability, reliability, and cost effectiveness. Fingerprints are generally considered the most practical biometric identifier in use today. Biometric Authentication Mode The way biometric data (e.g. fingerprints) is used for authentication. The mode chosen for a biometric installation depends on the specific needs of a site, where either convenience or security may be emphasized. BioCert fingerprint devices may use either of two biometric authentication modes, identification or verification. Biometric template Biometric templates are representations of a fingerprint or other biometric using series of numbers and letters. Templates are created using sophisticated algorithms, a mathematical process. Contactless card Smart cards or memory cards which communicate by a radio signal. The range is normally up to 10 cm from the reader. Dual Interface Card Dual interface cards have contact and contact less interfaces for data and transmission in both directions. Encryption Making information unreadable/difficult-to read for unauthorized persons. Enrolling The process of collecting biometric data from the individual, which is later, processed and stored as a template.
False Rejection Rate Also known as FRR. Measures how frequently registered users are rejected by the system. This usually amounts to nothing more than inconvenience, since it requires users to try again. The FRR of BioCert devices is currently about .01% and is usually improved by educating users on correct usage of fingerprint recognition devices, especially in high security environments. FIPS 201 Federal Information Processing Standards 201 creates the framework from the smart card security for PIV IDs. The US General Services Administrationís (GSA) Approved Products List (APL), is an important requirement in the procurement process for the US Federal Government Homeland Security Presidential Directive 12 (HSPD-12). By fall this year all US Government agencies must initiate the deployment of smart card based ID cards, the so-called PIV (Personal Identity Verification) Cards. GSA APL In order to eliminate the need for every agency to test and certify products to implement into HSPD-12, The General Services Administration (GSA) was asked to create an Approved Products List (APL). The GSA APL will serve as the buying guide for all of the US Federal Government Agencies. As agencies begin to implement their HSPD-12 and PIV solutions they will use the GSA APL to provide assurance that the products they are purchasing meet guidelines and technical specifications. HSPD-12 Abbreviation for US Federal government's Homeland Security Presidential Directive, which is a set of requirements for government agencies to improve their security infrastructure.
ISO International Organization for Standardization. Latent Fingerprint Latent fingerprints are "left over" fragments usually caused by the build-up of oily residues on the optic sensor window after repeated use. The technique used by BioCert devices to defeat "faked" fingerprints also prevents latent fingerprints from being incorrectly validated by the system.
Matching Method Algorithms for Fingerprint ID Systems:
Mifare Mifare is an interface for contact less smart cards and smart card readers. It has been developed by Philips and influencing the ISO14443 Standard. Minutiae The unique, measurable physical characteristics scanned as input and stored for matching by biometric systems. For fingerprints, minutiae include the starting and ending points of ridges, bifurcations and ridge junctions among other features. NIST Abbreviation for the National Institute for Standardization of Technology, which is an agency of the US Federal Government which establishes standards and guidelines for private and public sector purposes. PIV-card Personal Identity Verification Card required to be issued to all US Federal employees and contractors under HSPD-12. SHA-1 SHA-1, published in 1995, is a hash algorithm designed by the NSA. The size of the output of this algorithm is 160 bits. In 2005, a theoretical method was published to find collisions in SHA-1 with effort smaller than that required for brute force on average (263 instead of 280 steps).Smart card A smart card is a plastic card, which holds a processing chip Ė like those found in computers. The chip on the card is designed to protect the information stored on it using various security mechanisms. Strong Passwords (Wikipedia) - A strong password is sufficiently long, random, or otherwise producible only by the user who chose it, that successfully guessing it will require too long a time. The length of time deemed to be too long will vary with the attacker, the attacker's resources, the ease with which a password can be tried, and the value of the password to the attacker. A student's password might not be worth more than a few seconds of computer time, whilst a password controlling access to a large bank's electronic money transfer system might be worth many weeks of computer time. Examples of stronger passwords include:
Template The biometric reference pattern of a person stored for matching. BioCert devices convert fingerprint minutiae into mathematical templates, so actual fingerprint images are not stored and cannot be reconstructed based on template data. Tokens A physical device that an authorized user of computer services is given to aid in authentication. Hardware tokens are often small enough to be carried in a pocket or purse. Some may store cryptographic keys, like a digital signature, or biometric data, like a fingerprint. Types of Fingerprint Readers There are several different types of fingerprint readers that are each designed for a different task with varying functionality and reliability. They are generally divided into two segments - Optical and Capacitance which refers to the technology being used to capture the minutiae or pattern matching data and are either Touch Sensors or Swipe Sensors which refers to the method of obtaining the fingerprint data.
Copyright Authentec Corporation - Used under FAIR USE as an
Authorized Reseller of Authentec Sensors
|
|||||||||||||||||||
|
Copyright © 2002-20012 Artemis
Solutions Group, Use of this site or purchase subject to these
Terms and
Conditions of use. Some images used on this website are Copyright (c) Comstock and used under license. |


 How
secure is 128bit AES Encryption? Assuming that you
could build a supercomputer that could "crack" a single DES
(Data Encryption Standard) key in a second (i.e., by using a
brute force method to try 255 keys per second),
then it would take that supercomputer approximately 149
thousand-billion (149 trillion) years to crack a 128-bit AES
key. To put that into perspective, the universe is believed
to be less than 20 billion years old. Grab a cup of
coffee, pack a lunch - this will take a while.
"According to the NIST - AES has the potential to remain
secure well beyond the next twenty years."
How
secure is 128bit AES Encryption? Assuming that you
could build a supercomputer that could "crack" a single DES
(Data Encryption Standard) key in a second (i.e., by using a
brute force method to try 255 keys per second),
then it would take that supercomputer approximately 149
thousand-billion (149 trillion) years to crack a 128-bit AES
key. To put that into perspective, the universe is believed
to be less than 20 billion years old. Grab a cup of
coffee, pack a lunch - this will take a while.
"According to the NIST - AES has the potential to remain
secure well beyond the next twenty years."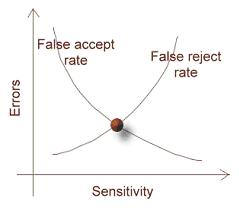 False
Acceptance Rate Also known as
False
Acceptance Rate Also known as 

 These passwords are longer and use combinations of lower and
upper case letters, digits, and symbols. They are unlikely to be
in any password cracking word list and are sufficiently long to
make direct brute force search impractical in some systems. Note
that some systems do not allow symbols like #, @
and ! in passwords and they may be hard to find on
different
These passwords are longer and use combinations of lower and
upper case letters, digits, and symbols. They are unlikely to be
in any password cracking word list and are sufficiently long to
make direct brute force search impractical in some systems. Note
that some systems do not allow symbols like #, @
and ! in passwords and they may be hard to find on
different

